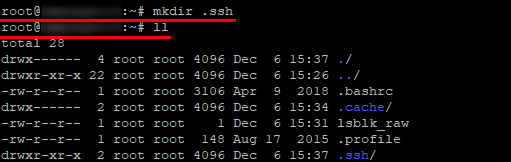
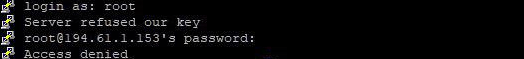Putty raw что это
Ларискины записки.
О чем тут? Да обо всем подряд. Это моя записная книжка. В основном тут бэкапы заинтересовавших меня статей, новости и ссылки.
О чем тут? Да обо всем подряд. Это моя записная книжка. В основном тут бэкапы заинтересовавших меня статей, новости и ссылки.
Работаем с PuTTY из Windows
Работаем с PuTTY из Windows
Putty это несколько отдельных программ, предназначенных для работы с unix-сервером по протоколам SSH1, SSH2, Telnet, Rlogin, Raw. Автором PuTTY является Simon Tatham. Программа работает на Win для Intel x86 и Alpha, а также на UNIX. Несмотря, на то что программа довольно популярна во всем мире, статей по практической работе с ней я не нашел, тем более что есть ньюансы, которые нужно учитывать. Чтобы устранить этот пробел и написана данная статья. Итак, полный комплект программ, под общим названием putty, состоит из нескольких утилит, их назначение вы видите ниже:
Установка
Скачайте с домашней странице PuTTY последнюю версию программы или только те утилиты, которые вам нужны для работы. Устанавливать putty необязательно, можно просто скопировать файлы в нужную директорию. Я например, храню комплект putty на флешке и ношу его с собой.
Создание пары ключей
Для укрепления безопасности, при работе с сервером, лучше отключить вход по паролю и создать ключи с ключевой парольной фразой. Для этого предназначена утилита puttygen.exe, внешний вид которой вы видите на экране. После запуска, установите тип создаваемых ключей SSH1(RSA), SSH2(RSA) или SSH2(DSA), говорят что SSH2(RSA) самый защищенный. Теперь нужно выбрать длину ключа в битах, по умолчанию там установлено 1024. Меньшее значение установить можно, но SSH2 сервер работать с короткими ключами не будет. Я не рекомендую использовать стандартные длины ключей типа 1024, 2048, 4096 лучше измените длину случайным образом 1429, 2361, 3417 и т.д. Далее нажмите кнопку Generate и поводите мышкой по пустому KEY-полю, пока ползунок дойдет до конца, после этого будут сгенерированы два ключа.
Нажмите кнопку Save public key, для того чтобы записать на диск публичный ключ, назовем его rsa-pub. Этот файл вы скопируете на SSH сервер, для того чтобы он вас узнавал. Теперь нажмите Save private key, и запишите на диск ваш секретный ключ с именем rsa-priv который будет храниться только у вас и передавать его никуда не нужно. Парольную фразу, лучше создать, хотя можно работать и без нее, просто создайте ключ большей длины 3926бит например. Итак, на диске вы имеете два файла rsa-pub и rsa-priv.ppk. Если на сервере вы используете OpenSSH, то перед тем как вы скопируете rsa-pub на ваш удаленный сервер, нужно его скорректировать! Без этого, этот ключ не будет работать в unix системах с OpenSSH! Оригинальный файл rsa-pub, который был создан puttygen, выглядет так:
Удалите первую, вторую и последнюю строки из него, впереди напишите ssh-rsa затем пробел, далее идет код с убранными символами переноса строки, в конце один пробел. Выглядеть отредактированный файл rsa-pub, будет так:
ssh-rsa AAAAB3NzaC1yc2EAAAABJQAAAIEA0vzPSq4tpvZf12OSyd6Q+F+tAEFMSn8kC1eQfqIZ9 qCX2NNIJkYbtRrwZxLDTw4BR2zEuN+uHXZ4mepIKwtVHIUUiHoYUV8k/hXXNbO0UMk=
Вот теперь файл rsa-pub с публичным ключем, готов к отправке на удаленный unix сервер и работать он будет корректно. Можно сделать по другому, выделите ключ в окне KEY, затем создайте пустой файл командой copy con rsa-pub и нажмите F6, теперь скопируйте в файл rsa-pub ключ из буфера, результат тотже.
Вход на сервер
Зайти на сервер вы можете несколькими способами. Если вы заходите по паролю, можно указать его прямо в строке или ввести по запросу (что, прямо скажем, более безопасно, так как пароль указывается в открытом виде), вот как будут выглядеть эти команды:
Пересылка файла
При работе с сервером, периодически возникает необходимость передать файл на сервер или принять файл с сервера. Сделать это можно утилитами pscp.exe и psftp.exe. На мой взгляд, pscp.exe использовать удобнее. Ниже смотрим на пример, который показывает, как можно по защищенному каналу, переслать файл stat0211.tgz из своего ПК на удаленный сервер:
При выполнении команды в таком виде, сервер запросит пароль. Чтобы это избежать можно добавить строку с паролем
Подключение к серверу через Putty: примеры использования
Сейчас читают:
Содержание
Применение и возможности PuTTY
PuTTY — программа, которая позволяет установить соединение с удаленным сервером или компьютером. Программу можно также применять для реализации следующих целей:
Работать рекомендуется через SSH, поскольку он обеспечивает высокий уровень безопасности соединения с другим компьютером. PuTTY поддерживает Telnet, реализующий текстовый интерфейс в терминале (только для отображения текстовой информации в режиме консоли).
Возможности программы
Установка на Windows
Работа с программой
Интерфейс
Соединение с удаленным сервером
Принцип подключения не зависит от операционной системы. Это могут быть разные версии Windows (7, 10) или популярные дистрибутивы на основе Linux — Ubuntu, CentOS, Debian.
Подключиться по SSH через PuTTY просто. Для этого нужно следовать приведенной ниже инструкции.
После этого работа с терминалом осуществляется, как на локальном компьютере. Чтобы узнать информацию о версии Ubuntu, нужно ввести команду:
Для удобства можно создать жесткую ссылку (ярлык) на программу для быстрого запуска.
Использование SSH-ключей
Шаг №1
Для начала, нужно выполнить ряд действий на компьютере с ОС Windows.
Шаг №2
Далее необходимо перенести SSH-ключ на сервер Ubuntu, выполнив перечисленные ниже действия.
Шаг №3
Возвращаемся к программе PuTTY на Windows 10.
Работа с файлами
Если для соединения используется нестандартный порт (например, 25), то команда примет вид:
Скачать файл через PuTTY с сервера « 192.241.7.16 » в текущую папку можно с помощью команды:
Распространенные ошибки
Проблемы с аутентификацией
PuTTY выдает при подключении сообщение: « Access denied». Это указывает на отказ в доступе, причиной которого являются ошибки при вводе логина или пароля.
Если соединение с удаленным сервером происходит при помощи SSH-ключа, то PuTTY выдаст в диалоговом окне такие строки:
Причины ошибки
Ошибка « Access denied » связана с некорректной аутентификацией на основе ключей. Вызвать ее может отсутствие соответствующих прав доступа к файлам или невозможность подтвердить права владельца.
Как решить
Подробнее о том, как создать удаленное соединение для разных дистрибутивов Linux, можно узнать из отдельных руководств:
Ошибка подключения
При истекшем времени подключения или отказе в соединении PuTTY выдаст сообщения « Network error: Connection timed out » и « Network error: Connection refused » соответственно.
Причины ошибки
Как решить
Начни экономить на хостинге сейчас — 14 дней бесплатно!
Глава 3: Using PuTTY
This chapter provides a general introduction to some more advanced features of PuTTY. For extreme detail and reference purposes, chapter 4 is likely to contain more information.
3.1 During your session
A lot of PuTTY’s complexity and features are in the configuration panel. Once you have worked your way through that and started a session, things should be reasonably simple after that. Nevertheless, there are a few more useful features available.
3.1.1 Copying and pasting text
Often in a PuTTY session you will find text on your terminal screen which you want to type in again. Like most other terminal emulators, PuTTY allows you to copy and paste the text rather than having to type it again. Also, copy and paste uses the Windows clipboard, so that you can paste (for example) URLs into a web browser, or paste from a word processor or spreadsheet into your terminal session.
By default, PuTTY’s copy and paste works entirely with the mouse. (This will be familiar to people who have used xterm on Unix.) In order to copy text to the clipboard, you just click the left mouse button in the terminal window, and drag to select text. When you let go of the button, the text is automatically copied to the clipboard. You do not need to press Ctrl-C or Ctrl-Ins; in fact, if you do press Ctrl-C, PuTTY will send a Ctrl-C character down your session to the server where it will probably cause a process to be interrupted.
Pasting into PuTTY is done using the right button (or the middle mouse button, if you have a three-button mouse and have set it up; see section 4.11.1). (Pressing Shift-Ins, or selecting «Paste» from the Ctrl+right-click context menu, have the same effect.) When you click the right mouse button, PuTTY will read whatever is in the Windows clipboard and paste it into your session. By default, this behaves exactly as if the clipboard contents had been typed at the keyboard; therefore, be careful of pasting formatted text into an editor that does automatic indenting, as you may find that the spaces pasted from the clipboard plus the spaces added by the editor add up to too many spaces and ruin the formatting. (Some remote applications can ask PuTTY to identify text that is being pasted, to avoid this sort of problem; but if your application does not, there is nothing PuTTY can do to avoid this.)
If you double-click the left mouse button, PuTTY will select a whole word. If you double-click, hold down the second click, and drag the mouse, PuTTY will select a sequence of whole words. (You can adjust precisely what PuTTY considers to be part of a word; see section 4.12.1.) If you triple-click, or triple-click and drag, then PuTTY will select a whole line or sequence of lines.
If you want to select a rectangular region instead of selecting to the end of each line, you can do this by holding down Alt when you make your selection. You can also configure rectangular selection to be the default, and then holding down Alt gives the normal behaviour instead: see section 4.11.3 for details.
(In some Unix environments, Alt+drag is intercepted by the window manager. Shift+Alt+drag should work for rectangular selection as well, so you could try that instead.)
If you have a middle mouse button, then you can use it to adjust an existing selection if you selected something slightly wrong. (If you have configured the middle mouse button to paste, then the right mouse button does this instead.) Click the button on the screen, and you can pick up the nearest end of the selection and drag it to somewhere else.
If you are running PuTTY itself on Unix (not just using it to connect to a Unix system from Windows), by default you will likely have to use similar mouse actions in other applications to paste the text you copied from PuTTY, and to copy text for pasting into PuTTY; actions like Ctrl-C and Ctrl-V will likely not behave as you expect. Section 4.11.4 explains why this is, and how you can change the behaviour. (On Windows there is only a single selection shared with other applications, so this confusion does not arise.)
It’s possible for the server to ask to handle mouse clicks in the PuTTY window itself. If this happens, the mouse pointer will turn into an arrow, and using the mouse to copy and paste will only work if you hold down Shift. See section 4.6.2 and section 4.11.2 for details of this feature and how to configure it.
You can customise much of this behaviour, for instance to enable copy and paste from the keyboard; see section 4.11.
3.1.2 Scrolling the screen back
PuTTY keeps track of text that has scrolled up off the top of the terminal. So if something appears on the screen that you want to read, but it scrolls too fast and it’s gone by the time you try to look for it, you can use the scrollbar on the right side of the window to look back up the session history and find it again.
As well as using the scrollbar, you can also page the scrollback up and down by pressing Shift-PgUp and Shift-PgDn. You can scroll a line at a time using Ctrl-PgUp and Ctrl-PgDn, or to the top/bottom of the scrollback with Ctrl-Shift-PgUp and Ctrl-Shift-PgDn. These are still available if you configure the scrollbar to be invisible.
By default the last 2000 lines scrolled off the top are preserved for you to look at. You can increase (or decrease) this value using the configuration box; see section 4.7.3.
3.1.3 The System menu
If you click the left mouse button on the icon in the top left corner of PuTTY’s terminal window, or click the right mouse button on the title bar, you will see the standard Windows system menu containing items like Minimise, Move, Size and Close.
PuTTY’s system menu contains extra program features in addition to the Windows standard options. These extra menu commands are described below.
(These options are also available in a context menu brought up by holding Ctrl and clicking with the right mouse button anywhere in the PuTTY window.)
3.1.3.1 The PuTTY Event Log
If you choose «Event Log» from the system menu, a small window will pop up in which PuTTY logs significant events during the connection. Most of the events in the log will probably take place during session startup, but a few can occur at any point in the session, and one or two occur right at the end.
You can use the mouse to select one or more lines of the Event Log, and hit the Copy button to copy them to the clipboard. If you are reporting a bug, it’s often useful to paste the contents of the Event Log into your bug report.
(The Event Log is not the same as the facility to create a log file of your session; that’s described in section 3.2.)
3.1.3.2 Special commands
Depending on the protocol used for the current session, there may be a submenu of «special commands». These are protocol-specific tokens, such as a «break» signal, that can be sent down a connection in addition to normal data. Their precise effect is usually up to the server. Currently only Telnet, SSH, and serial connections have special commands.
The «break» signal can also be invoked from the keyboard with Ctrl-Break.
In an SSH connection, the following special commands are available:
Should have no effect.
Only available in SSH-2. Forces a repeat key exchange immediately (and resets associated timers and counters). For more information about repeat key exchanges, see section 4.20.2.
Only available in SSH-2. This submenu appears only if the server has host keys of a type that PuTTY doesn’t already have cached, and so won’t consider. Selecting a key here will allow PuTTY to use that key now and in future: PuTTY will do a fresh key-exchange with the selected key, and immediately add that key to its permanent cache (relying on the host key used at the start of the connection to cross-certify the new key). That key will be used for the rest of the current session; it may not actually be used for future sessions, depending on your preferences (see section 4.21.1).
Normally, PuTTY will carry on using a host key it already knows, even if the server offers key formats that PuTTY would otherwise prefer, to avoid host key prompts. As a result, if you’ve been using a server for some years, you may still be using an older key than a new user would use, due to server upgrades in the meantime. The SSH protocol unfortunately does not have organised facilities for host key migration and rollover, but this allows you to manually upgrade.
Only available in SSH-2, and only during a session. Optional extension; may not be supported by server. PuTTY requests the server’s default break length.
Only available in SSH-2, and only during a session. Sends various POSIX signals. Not honoured by all servers.
The following special commands are available in Telnet:
PuTTY can also be configured to send this when the Backspace key is pressed; see section 4.17.3.
Should have no effect.
PuTTY can also be configured to send this when Ctrl-C is typed; see section 4.17.3.
PuTTY can also be configured to send this when Ctrl-Z is typed; see section 4.17.3.
With a serial connection, the only available special command is «Break».
3.1.3.3 Starting new sessions
PuTTY’s system menu provides some shortcut ways to start new sessions:
3.1.3.4 Changing your session settings
If you select «Change Settings» from the system menu, PuTTY will display a cut-down version of its initial configuration box. This allows you to adjust most properties of your current session. You can change the terminal size, the font, the actions of various keypresses, the colours, and so on.
Some of the options that are available in the main configuration box are not shown in the cut-down Change Settings box. These are usually options which don’t make sense to change in the middle of a session (for example, you can’t switch from SSH to Telnet in mid-session).
You can save the current settings to a saved session for future use from this dialog box. See section 4.1.2 for more on saved sessions.
3.1.3.5 Copy All to Clipboard
This system menu option provides a convenient way to copy the whole contents of the terminal screen (up to the last nonempty line) and scrollback to the clipboard in one go.
3.1.3.6 Clearing and resetting the terminal
The «Clear Scrollback» option on the system menu tells PuTTY to discard all the lines of text that have been kept after they scrolled off the top of the screen. This might be useful, for example, if you displayed sensitive information and wanted to make sure nobody could look over your shoulder and see it. (Note that this only prevents a casual user from using the scrollbar to view the information; the text is not guaranteed not to still be in PuTTY’s memory.)
The «Reset Terminal» option causes a full reset of the terminal emulation. A VT-series terminal is a complex piece of software and can easily get into a state where all the text printed becomes unreadable. (This can happen, for example, if you accidentally output a binary file to your terminal.) If this happens, selecting Reset Terminal should sort it out.
3.1.3.7 Full screen mode
If you find the title bar on a maximised window to be ugly or distracting, you can select Full Screen mode to maximise PuTTY «even more». When you select this, PuTTY will expand to fill the whole screen and its borders, title bar and scrollbar will disappear. (You can configure the scrollbar not to disappear in full-screen mode if you want to keep it; see section 4.7.3.)
When you are in full-screen mode, you can still access the system menu if you click the left mouse button in the extreme top left corner of the screen.
3.2 Creating a log file of your session
For some purposes you may find you want to log everything that appears on your screen. You can do this using the «Logging» panel in the configuration box.
To begin a session log, select «Change Settings» from the system menu and go to the Logging panel. Enter a log file name, and select a logging mode. (You can log all session output including the terminal control sequences, or you can just log the printable text. It depends what you want the log for.) Click «Apply» and your log will be started. Later on, you can go back to the Logging panel and select «Logging turned off completely» to stop logging; then PuTTY will close the log file and you can safely read it.
See section 4.2 for more details and options.
3.3 Altering your character set configuration
If you find that special characters (accented characters, for example, or line-drawing characters) are not being displayed correctly in your PuTTY session, it may be that PuTTY is interpreting the characters sent by the server according to the wrong character set. There are a lot of different character sets available, and no good way for PuTTY to know which to use, so it’s entirely possible for this to happen.
If you click «Change Settings» and look at the «Translation» panel, you should see a large number of character sets which you can select, and other related options. Now all you need is to find out which of them you want! (See section 4.10 for more information.)
3.4 Using X11 forwarding in SSH
The SSH protocol has the ability to securely forward X Window System graphical applications over your encrypted SSH connection, so that you can run an application on the SSH server machine and have it put its windows up on your local machine without sending any X network traffic in the clear.
In order to use this feature, you will need an X display server for your Windows machine, such as Cygwin/X, X-Win32, or Exceed. This will probably install itself as display number 0 on your local machine; if it doesn’t, the manual for the X server should tell you what it does do.
Now you should be able to log in to the SSH server as normal. To check that X forwarding has been successfully negotiated during connection startup, you can check the PuTTY Event Log (see section 3.1.3.1). It should say something like this:
If the remote system is Unix or Unix-like, you should also be able to see that the DISPLAY environment variable has been set to point at display 10 or above on the SSH server machine itself:
If this works, you should then be able to run X applications in the remote session and have them display their windows on your PC.
For more options relating to X11 forwarding, see section 4.26.
3.5 Using port forwarding in SSH
The SSH protocol has the ability to forward arbitrary network (TCP) connections over your encrypted SSH connection, to avoid the network traffic being sent in clear. For example, you could use this to connect from your home computer to a POP-3 server on a remote machine without your POP-3 password being visible to network sniffers.
In order to use port forwarding to connect from your local machine to a port on a remote server, you need to:
Now start your session and log in. (Port forwarding will not be enabled until after you have logged in; otherwise it would be easy to perform completely anonymous network attacks, and gain access to anyone’s virtual private network.) To check that PuTTY has set up the port forwarding correctly, you can look at the PuTTY Event Log (see section 3.1.3.1). It should say something like this:
You can also forward ports in the other direction: arrange for a particular port number on the server machine to be forwarded back to your PC as a connection to a service on your PC or near it. To do this, just select the «Remote» radio button instead of the «Local» one. The «Source port» box will now specify a port number on the server (note that most servers will not allow you to use port numbers under 1024 for this purpose).
An alternative way to forward local connections to remote hosts is to use dynamic SOCKS proxying. In this mode, PuTTY acts as a SOCKS server, which SOCKS-aware programs can connect to and open forwarded connections to the destination of their choice, so this can be an alternative to long lists of static forwardings. To use this mode, you will need to select the «Dynamic» radio button instead of «Local», and then you should not enter anything into the «Destination» box (it will be ignored). PuTTY will then listen for SOCKS connections on the port you have specified. Most web browsers can be configured to connect to this SOCKS proxy service; also, you can forward other PuTTY connections through it by setting up the Proxy control panel (see section 4.16 for details).
The source port for a forwarded connection usually does not accept connections from any machine except the SSH client or server machine itself (for local and remote forwardings respectively). There are controls in the Tunnels panel to change this:
For more options relating to port forwarding, see section 4.27.
If the connection you are forwarding over SSH is itself a second SSH connection made by another copy of PuTTY, you might find the «logical host name» configuration option useful to warn PuTTY of which host key it should be expecting. See section 4.14.5 for details of this.
3.6 Making raw TCP connections
A lot of Internet protocols are composed of commands and responses in plain text. For example, SMTP (the protocol used to transfer e-mail), NNTP (the protocol used to transfer Usenet news), and HTTP (the protocol used to serve Web pages) all consist of commands in readable plain text.
Sometimes it can be useful to connect directly to one of these services and speak the protocol «by hand», by typing protocol commands and watching the responses. On Unix machines, you can do this using the system’s telnet command to connect to the right port number. For example, telnet mailserver.example.com 25 might enable you to talk directly to the SMTP service running on a mail server.
Although the Unix telnet program provides this functionality, the protocol being used is not really Telnet. Really there is no actual protocol at all; the bytes sent down the connection are exactly the ones you type, and the bytes shown on the screen are exactly the ones sent by the server. Unix telnet will attempt to detect or guess whether the service it is talking to is a real Telnet service or not; PuTTY prefers to be told for certain.
In order to make a debugging connection to a service of this type, you simply select the fourth protocol name, «Raw», from the «Protocol» buttons in the «Session» configuration panel. (See section 4.1.1.) You can then enter a host name and a port number, and make the connection.
3.7 Connecting to a local serial line
PuTTY can connect directly to a local serial line as an alternative to making a network connection. In this mode, text typed into the PuTTY window will be sent straight out of your computer’s serial port, and data received through that port will be displayed in the PuTTY window. You might use this mode, for example, if your serial port is connected to another computer which has a serial connection.
To make a connection of this type, simply select «Serial» from the «Connection type» radio buttons on the «Session» configuration panel (see section 4.1.1). The «Host Name» and «Port» boxes will transform into «Serial line» and «Speed», allowing you to specify which serial line to use (if your computer has more than one) and what speed (baud rate) to use when transferring data. For further configuration options (data bits, stop bits, parity, flow control), you can use the «Serial» configuration panel (see section 4.29).
After you start up PuTTY in serial mode, you might find that you have to make the first move, by sending some data out of the serial line in order to notify the device at the other end that someone is there for it to talk to. This probably depends on the device. If you start up a PuTTY serial session and nothing appears in the window, try pressing Return a few times and see if that helps.
A serial line provides no well defined means for one end of the connection to notify the other that the connection is finished. Therefore, PuTTY in serial mode will remain connected until you close the window using the close button.
3.8 The PuTTY command line
PuTTY can be made to do various things without user intervention by supplying command-line arguments (e.g., from a command prompt window, or a Windows shortcut).
3.8.1 Starting a session from the command line
These options allow you to bypass the configuration window and launch straight into a session.
To start a connection to a server called host :
If this syntax is used, settings are taken from the Default Settings (see section 4.1.2); user overrides these settings if supplied. Also, you can specify a protocol, which will override the default protocol (see section 3.8.3.2).
For telnet sessions, the following alternative syntax is supported (this makes PuTTY suitable for use as a URL handler for telnet URLs in web browsers):
To start a connection to a serial port, e.g. COM1:
3.8.3 Standard command-line options
PuTTY and its associated tools support a range of command-line options, most of which are consistent across all the tools. This section lists the available options in all tools. Options which are specific to a particular tool are covered in the chapter about that tool.
You need double quotes around the session name if it contains spaces.
If you want to create a Windows shortcut to start a PuTTY saved session, this is the option you should use: your shortcut should call something like
To choose which protocol you want to connect with, you can use one of these options:
These options are not available in the file transfer tools PSCP and PSFTP (which only work with the SSH protocol).
These options are equivalent to the protocol selection buttons in the Session panel of the PuTTY configuration box (see section 4.1.1).
These options are equivalent to the username selection box in the Connection panel of the PuTTY configuration box (see section 4.15.1).
As well as setting up port forwardings in the PuTTY configuration (see section 4.27), you can also set up forwardings on the command line. The command-line options work just like the ones in Unix ssh programs.
To forward a local port (say 5110) to a remote destination (say popserver.example.com port 110), you can write something like one of these:
To specify an IP address for the listening end of the tunnel, prepend it to the argument:
For general information on port forwarding, see section 3.5.
These options are not available in the file transfer tools PSCP and PSFTP.
With some servers (particularly Unix systems), you can even put multiple lines in this file and execute more than one command in sequence, or a whole shell script; but this is arguably an abuse, and cannot be expected to work on all servers. In particular, it is known not to work with certain «embedded» servers, such as Cisco routers.
This option is not available in the file transfer tools PSCP and PSFTP.
This option is equivalent to the port number control in the Session panel of the PuTTY configuration box (see section 4.1.1).
A simple way to automate a remote login is to supply your password on the command line. This is not recommended for reasons of security. If you possibly can, we recommend you set up public-key authentication instead. See chapter 8 for details.
See chapter 9 for general information on Pageant.
These options are equivalent to the agent authentication checkbox in the Auth panel of the PuTTY configuration box (see section 4.23.3).
See chapter 9 for general information on Pageant, and section 9.4 for information on agent forwarding. Note that there is a security risk involved with enabling this option; see section 9.5 for details.
These options are equivalent to the agent forwarding checkbox in the Auth panel of the PuTTY configuration box (see section 4.23.6).
These options are not available in the file transfer tools PSCP and PSFTP.
For information on X11 forwarding, see section 3.4.
These options are equivalent to the X11 forwarding checkbox in the X11 panel of the PuTTY configuration box (see section 4.26).
These options are not available in the file transfer tools PSCP and PSFTP.
These options are equivalent to the «Don’t allocate a pseudo-terminal» checkbox in the SSH panel of the PuTTY configuration box (see section 4.25.1).
These options are not available in the file transfer tools PSCP and PSFTP.
This feature is only available in SSH protocol version 2 (since the version 1 protocol assumes you will always want to run a shell).
This option is equivalent to the «Don’t start a shell or command at all» checkbox in the SSH panel of the PuTTY configuration box (see section 4.19.2).
This option is not available in the file transfer tools PSCP and PSFTP.
This option is equivalent to the «Enable compression» checkbox in the SSH panel of the PuTTY configuration box (see section 4.19.3).
These options are equivalent to selecting the SSH protocol version in the SSH panel of the PuTTY configuration box (see section 4.19.4).
These options are equivalent to selecting your preferred Internet protocol version as «IPv4» or «IPv6» in the Connection panel of the PuTTY configuration box (see section 4.14.4).
If you are using Pageant, you can also specify a public key file (in RFC 4716 or OpenSSH format) to identify a specific key file to use. (This won’t work if you’re not running Pageant, of course.)
For general information on public-key authentication, see chapter 8.
This option is equivalent to the «Private key file for authentication» box in the Auth panel of the PuTTY configuration box (see section 4.23.8).
This option overrides PuTTY’s normal SSH host key caching policy by telling it the name of the host you expect your connection to end up at (in cases where this differs from the location PuTTY thinks it’s connecting to). It can be a plain host name, or a host name followed by a colon and a port number. See section 4.14.5 for more detail on this.
This option overrides PuTTY’s normal SSH host key caching policy by telling it exactly what host key to expect, which can be useful if the normal automatic host key store in the Registry is unavailable. The argument to this option should be either a host key fingerprint, or an SSH-2 public key blob. See section 4.21.2 for more information.
You can specify this option more than once if you want to configure more than one key to be accepted.
This option causes the PuTTY tools not to run as normal, but instead to display the fingerprints of the PuTTY PGP Master Keys, in order to aid with verifying new versions. See appendix E for more information.
This option specifies the configuration parameters for the serial port (baud rate, stop bits etc). Its argument is interpreted as a comma-separated list of configuration options, which can be as follows:
For more information on logging configuration, see section 4.2.
This option enables PuTTY’s mode for running a command on the local machine and using it as a proxy for the network connection. It expects a shell command string as an argument.
See section 4.16.1 for more information on this, and on other proxy settings. In particular, note that since the special sequences described there are understood in the argument string, literal backslashes must be doubled (if you want \ in your command, you must put \\ on the command line).
This option (on Windows only) causes PuTTY (or another PuTTY tool) to try to lock down the operating system’s access control on its own process. If this succeeds, it should present an extra obstacle to malware that has managed to run under the same user id as the PuTTY process, by preventing it from attaching to PuTTY using the same interfaces debuggers use and either reading sensitive information out of its memory or hijacking its network session.
This option is not enabled by default, because this form of interaction between Windows programs has many legitimate uses, including accessibility software such as screen readers. Also, it cannot provide full security against this class of attack in any case, because PuTTY can only lock down its own ACL after it has started up, and malware could still get in if it attacks the process between startup and lockdown. So it trades away noticeable convenience, and delivers less real security than you might want. However, if you do want to make that tradeoff anyway, the option is available.